By: IE Security Team on November 30th, 2017
10 Steps for Achieving Effective Vulnerability Management
Cybersecurity | Mobility & WiFi | Managed IT Services | Technology Solutions
We all know that the threat landscape isn’t getting any easier to manage. Fact is, most organizations don’t have the resources or the time to carry-out the endless activities that could reduce their exposure. However, there are a few things you can do that will make the most impact.
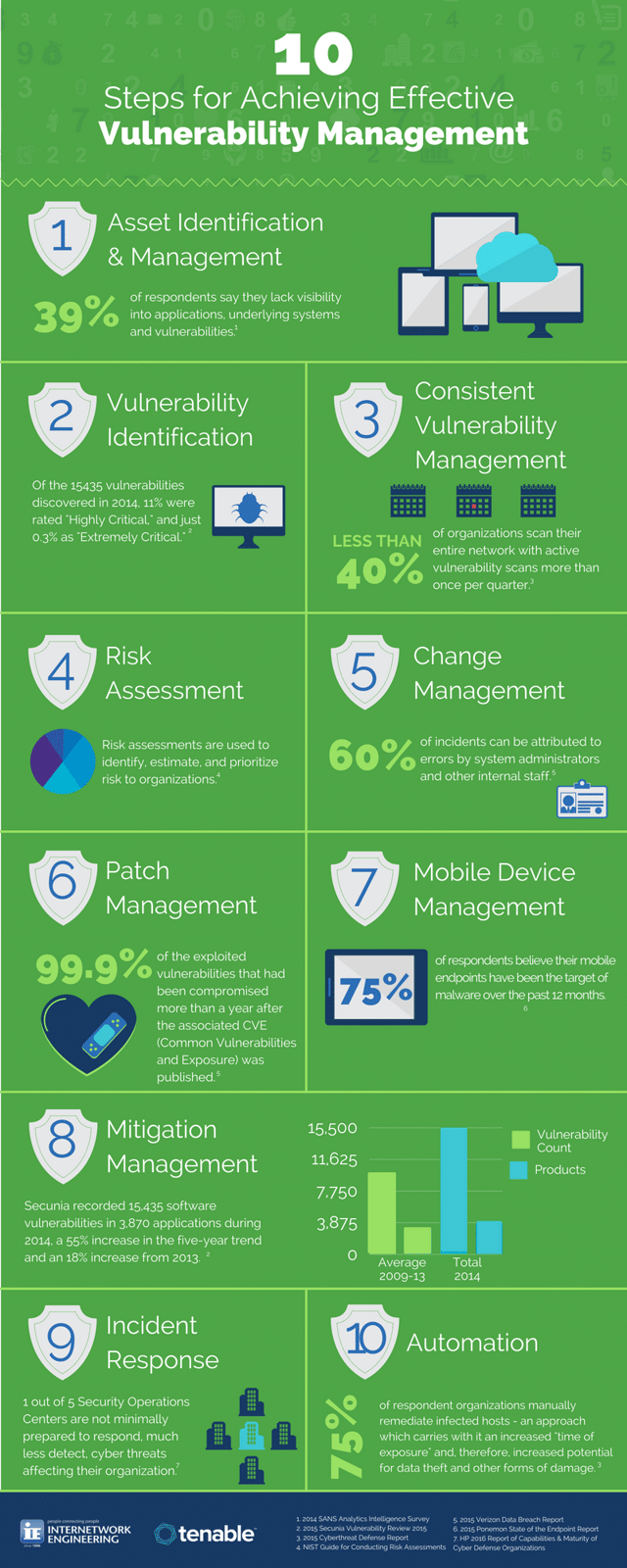
Our partners at Tenable helped us put together these 10 Steps to Effective Vulnerability Management.
If you’re ready to take these steps even further, check out this ebook, 10 Steps for Achieving Effective Vulnerability Management from Tenable. In it you’ll learn about:
- The challenges for vulnerability management
- Crucial weaknesses to look for
- 10 actions you can take to reduce vulnerabilities
- Key performance indicators
If you'd like more information on how IE can help your organization increase it’s security posture, please contact us and one of our Security Team members will reach out.